Intelligent Design:
Coin Operations and Intelligence Collection and Analysis
Majors Laura Geldhof, Maureen Green, Remi Hajjar, Chris Litwhiler, Christine Locke, James Myers, David Perrine, Cameron Weathers and Dan Zeytoonian
Download the PDF 
This article was originally published in Special Warfare, May–June 2006. It was written and reviewed by a team of officers in Class 2006-01 of the Command and General Staff Officer Course at Fort Leavenworth, Kansas. Contributors include Majors Laura Geldhof, Maureen Green, Remi Hajjar, Chris Litwhiler, Christine Locke, James Myers, David Perrine, Cameron Weathers and Dan Zeytoonian; Lieutenant Commander David Smith and Christine Watson. Zeytoonian is the primary author.
One of the greatest challenges for the current generation of American military professionals is relearning the principles of counterinsurgency (COIN). This includes intelligence professionals who must not only tailor the Intelligence Preparation of the Battlespace (IPB) process to the requirements of COIN, but also learn the intricacies of foreign cultures and peoples. Analysts have to shift their focus from military capabilities to social networks, culture, and people. The level of understanding required to conduct COIN operations at the tactical and operational levels presents challenges.
At the beginning of a COIN campaign, before patterns in the enemy’s method of operating have emerged, the intelligence analyst is more dependent on military art than science. In such a situation, to generate actionable intelligence, friendly forces must frequently begin by executing an action.1 In that type of operation, the role of intelligence shifts from one that supports maneuver to a more central role.
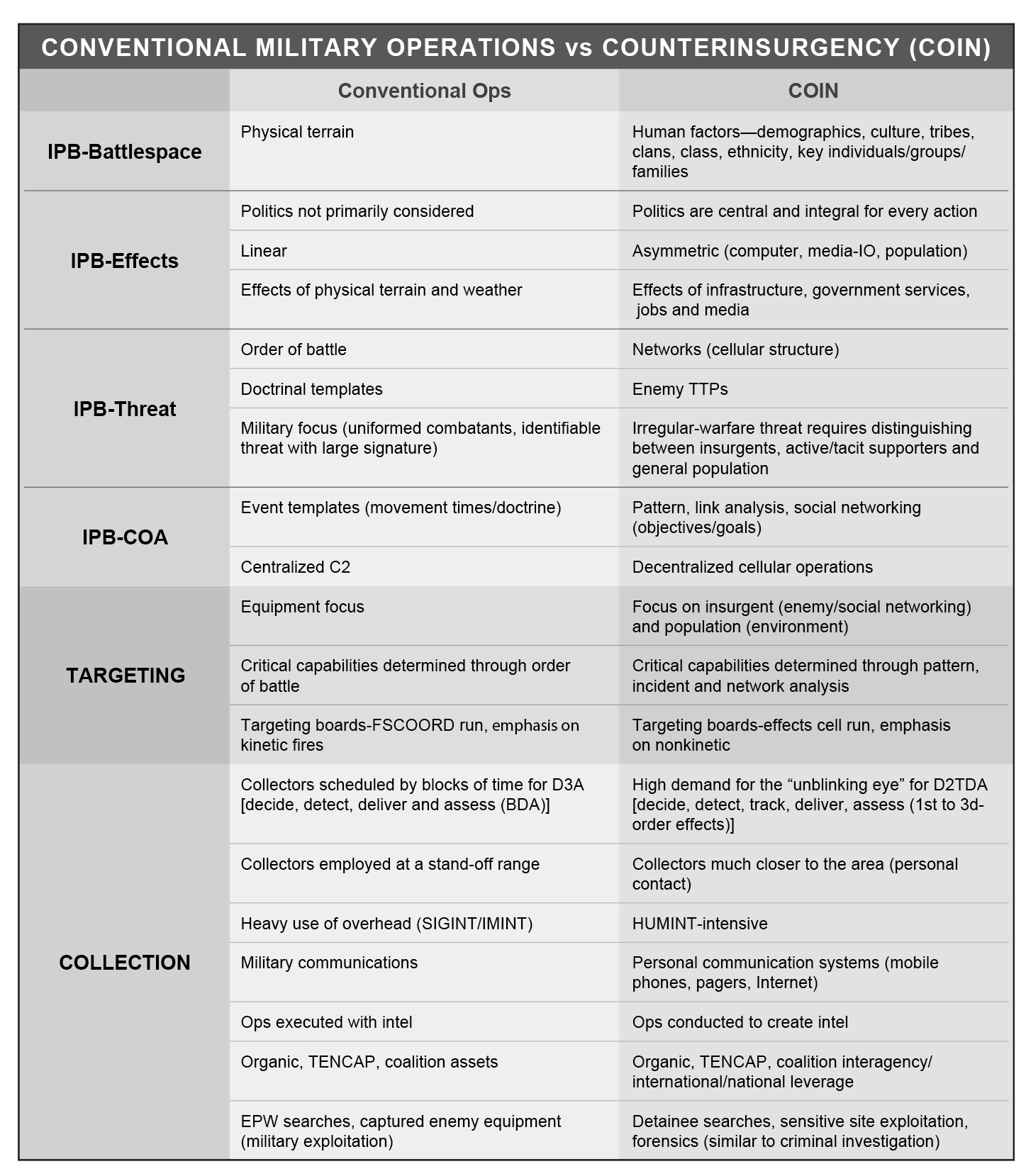
Perhaps the biggest intelligence challenges presented by COIN arise from the difficulties friendly forces face in identifying insurgents and in understanding complex cultural environments. Examples can be seen in the chart on the following page. Before discussing COIN, we must review IPB against more conventional threats to appreciate the changes in collection, analysis, and support to targeting.
Traditional Threats
For more than 40 years, the United States prepared for a conventional war against the Soviet Union and its allies. The cold war affected every facet of Army operations, from weapons procurement, to the development of tactics, to training at the combat training centers.
Cold war planning also affected the various parts of the intelligence cycle: direct, collect, process and disseminate. In developing the IPB process, the intelligence community utilized doctrinal templates that became the basis for the development of enemy Courses of Action (COA). The availability of Soviet doctrine, combined with their rigid adherence to it and the minimal amounts of initiative they afforded junior leaders, made the doctrinal templates a useful and accurate tool. Over time, IPB became a scientific process.
Collection. Collection of intelligence against enemy targets focused on the threat’s large networks, including command, control and communications; air defense; and sustainment. Intelligence assets at all levels utilized a balance of the various intel disciplines—human intelligence (HUMINT), signals intelligence (SIGINT), imagery intelligence (IMINT), and measurement and signatures intelligence (MASINT)—to find the enemy for targeting. Tactical and operational Military Intelligence (MI) units used their organic systems as well as Tactical Exploitation of National Capabilities (TENCAP) feeds to find concentrations of Soviet forces.
Analysis.Define the battlefield environment and describe the battlefield effects. In this part of IPB, the intelligence section focused on the effects of weather and the physical terrain on friendly and enemy operations. It focused on the military aspects of terrain, mobility and the impact of terrain on the range of the weapons systems.
Evaluate the threat and determine threat courses of action. Determining the effects of weather and terrain allowed an intelligence section to predict an enemy force’s scheme of maneuver in a situational template. Further adjustments were made by taking into account range fans, doctrinal rates of movement, and the space and time between echelons. Units that trained in exercises against this threat believed that the IPB process did a good job of depicting its operations. The reality, however, is that we may never know, because we never faced the Soviet Army in battle.
Targeting. Tactical targeting in conventional operations had a kinetic focus. Friendly forces targeted high-payoff targets that would weaken the enemy at a decisive point. These target sets traditionally included reconnaissance units, armor, engineer equipment, long-range artillery, rockets, and attack-aviation assets. At the operational level, the targeting effort focused on key enablers such as petroleum storage facilities, supply warehouses, and ammunition supply points. Additionally, using Information Operations (IO) and Psychological Operations (PSYOP), friendly forces tried to demoralize enemy forces and dissuade them from fighting and to influence other forces. During a conventional fight, intelligence supported most parts of the targeting process: decide, detect, deliver, and assess.
Intelligence Support to COIN
Supporting COIN operations with intelligence requires the analyst to know the indigenous people in a way not required by conventional operations. This human-intelligence dimension involves examining the role that culture, demographics, political support, religion, and ethnicity play. It also necessitates learning about patterns of social networking. The intelligence cycle begins with directing requirements to different intelligence assets and then conducting collection operations.
Collection. In the COIN environment, identifying the enemy is a significant obstacle and an important part of the collection process. Potential adversaries have the advantage of blending in with the population. Identifying insurgents must occur in order to separate the insurgents from their bases of support through population control.
The focus of collection efforts in COIN differs greatly from that of conventional combat operations. Because human factors are extremely important, standoff collection assets have less value. In COIN, useful intelligence is most often obtained through personal contact with the population. This puts a disproportionate level of importance on HUMINT and requires a different understanding of it. In conventional operations, HUMINT is the domain of interrogators and counterintelligence agents; that has changed.
In COIN, the preponderance of HUMINT comes from the units who have the most familiarity and contact with the population. Special Forces teams, Civil Affairs (CA) personnel, the unit chaplain, the commander, engineers, the squad automatic weapon gunner, and everybody else who has daily contact with the population notice changing conditions in their areas before anybody else. Some of the changes might match indicators and warnings from the intelligence section that precede an insurgent action. Input from first-contact units gives the commander the ability to see first, understand first, and act first. The increase in situational awareness helps friendly forces gain and maintain the initiative, which is critical in COIN.2
While COIN demands that we break our reliance on technical collection and put renewed emphasis on HUMINT, the other intelligence disciplines—SIGINT, IMINT, and MASINT—still have value. Friendly forces can take advantage of national collection assets using organic TENCAP systems to confirm or deny HUMINT reporting. As Colonel Rick Allenbaugh notes, “[In a COIN targeting cycle], the key is [still] cross-cueing and synchronization.”3 Open-Source Intelligence (OSINT) also gains a measure of importance that it does not have against a conventional threat. The intelligence analyst has much to gain from what people say on the radio and write in newspapers. Just gauging the number of pro- and anti-government newspapers printed in a certain area is telling.
The sources of intelligence and the collection assets that an intelligence professional has access to in a COIN environment are much different from those of a conventional combat operation. In a conventional operation, the intelligence section accesses organic assets with limited or no access to interagency, international, or national sources of information, especially at lower echelons. In COIN, intelligence operations strive to fuse intelligence from nonorganic collection sources into a seamless picture of the insurgency networks and to provide corroborating intelligence for targeting.
As noted by retired Major General James Marks, maneuver commanders are also conducting operations to gain intelligence: “Commanders at all levels must develop intelligence to develop their missions. Higher headquarters often will not and cannot provide sufficient clarity of task or purpose to drive operations at the lower levels.”4 As a result, intelligence operations are now considered operational missions. For example, operational elements may plan to increase patrols and establish roadblocks surrounding a neighborhood suspected of harboring Al-Qaeda senior leadership. Door-to-door checks through residences may trigger movement of a target that might be detected by unmanned aerial vehicles or by cordon-and-search forces when the target attempts to escape the area. Another example of the relational changes is the integration of intelligence professionals into information operations and the nonkinetic targeting processes.
Operators are now trained for and accustomed to collecting forensic evidence during search operations. During site exploitation, residences suspected of providing safe havens to insurgents are now treated much like crime scenes. Operators search for and collect items that may provide leads for future operations. As Allenbaugh notes, “Forensics are new and not fully accepted or understood.”5 Building a forensic case has two major benefits: It allows Host-Nation (HN) security forces to build legal cases against insurgents and their supporters; and it provides information that interrogators can use to confront suspects and gain more intelligence on their network and operational plans.
While COIN demands that we break our reliance on technical collection and put renewed emphasis on HUMINT, the other intelligence disciplines—SIGINT, IMINT, and MASINT —still have value.
The COIN environment requires joint, interagency, international and HN collaboration for collection operations and target development. National intelligence support teams, when deployed to an operational command, provide access to national-level collection assets from Other Government Agencies (OGAs). Joint Interagency Task Forces (JIATFs), composed of military and government intelligence analysts and collectors, offer another way of accessing national intelligence and analysis.6 Military analysts fuse that intelligence with organic collection to gain the best possible understanding of the insurgent network, high-value targets and the populace.
Centralized and synchronized intelligence collection between all elements deployed in a theater is important for providing a more complete picture of terrorist networking through more thorough intelligence fusion. In current operations, a target tracked by the JIATF in Afghanistan or Pakistan may carry operational plans between the Al-Qaeda senior leadership and other operatives, and later turn up in another command’s sector in Iraq. This makes mutual support between commands a necessity. The insurgent network is linked; we should be, too.
Mutual support between the various units, agencies, and countries often meets parochial and cultural roadblocks. Intelligence professionals must work cooperatively but forcefully to cut through bureaucratic red tape and to keep everybody focused on the end state: actionable intelligence. The synergy of intelligence collaboration is too valuable to sacrifice to petty concerns.

Analysis. Define the battlefield environment and describe the battlefield effects. One of the requirements in the first IPB step is to establish an Area of Interest (AI).7 Although U.S. forces face adversaries who conduct transnational operations and aspire to lead a global insurgency, the AI, as a practical matter, cannot be the entire world. Intelligence analysts work to incorporate local nodes that the insurgents use to connect with other parts of their network into the AI. Doing this creates an AI that encompasses a manageable area for analysis. These AIs may include avenues of approach that cross an international boundary and lines of communication, including known or likely courier routes, SIGINT networks and local Internet service providers.
Lieutenant Colonel David Kilcullen, in his article “Twenty-Eight Articles: Fundamentals of Company-level Counterinsurgency,” offers some valuable advice about studying the terrain: “Know the people, the topography, economy, history, religion and culture. Know every village, road, field, population group, tribal leader and ancient grievance. Your task is to become the world expert on your district.”8
Depending on the operational environment, a myriad of other demographic considerations may also become relevant in COIN. These considerations include social class structure, race, ethnicity, tribe, political party, gender, age, physical ability, nationality, language, religion, professional or occupational status, and employment levels. Additionally, key personnel and groups have become the new key terrain. These may comprise religious clerics, financially powerful families, influential members of the opposition, or anyone with influence over a large or important constituency. Insurgents may target, agitate, or subvert any of these groups to further their aims.
Key terrain also encompasses the neutral pockets of the population, the “fence sitters” who represent the operational center of gravity.9 Intelligence sections should graphically depict the geographic areas of these various groups in population status overlays and continuously develop the relationship of social networks using link diagrams. Population analysis enables military forces to identify key formal and informal leaders as well as groups of people who require intelligence and operational focus. This socio-cultural analysis bolsters the power of fullspectrum military operations by providing a starting point for winning “hearts and minds.”
An evaluation of the battlefield’s effects begins with an analysis of the environment and its effect on friendly and enemy operations. The analyst also considers political topography and the factors that relate to it. These may include infrastructure and enemy capabilities that previously were not evaluated. In the COIN environment, one must consider the importance of infrastructure and not merely its location and effect. Opening an office of a government ministry in a certain neighborhood could have second- and third-order effects that the commander must weigh when he considers COAs.
Owing to technology and the asymmetrical nature of the threat, the battlespace now heavily favors the use of information operations. Using cyberspace and the media, the insurgents seek to influence their target audience, expand their numbers, and exploit their acts. Outlets that allow the insurgents to spread their message must be incorporated into the analysis of the environment. COIN forces should pay attention to Internet pages, in particular, as they provide an effective means of reaching a large audience from an electronic sanctuary.
Evaluate the threat and determine threat courses of action. The requirements of steps 3 and 4 of IPB, as outlined in U.S. Army Field Manual 34-130, Intelligence Preparation of the Battlefield, show that the process is adaptable to COIN, although COIN presents additional challenges. Step 3 consists of converting patterns of operations to graphics, describing, in words, the threat’s tactics and options, identifying high-value targets (HVTs), and defining the threat capabilities.10
COIN forces must exercise operational patience and allow enough time for insurgent patterns of operation to emerge. Interrogations of detained insurgents and the exploitation of captured manuals, equipment, and information will also help to confirm suspected patterns of operation and tactics, techniques and procedures.
In assessing threat capabilities, the intelligence section will try to link personnel with events using an activities matrix. A series of incidents, along with information from captured personnel and equipment, may help reveal key personnel within the network. Examples may include bomb makers, financiers, and arms dealers. Their relative power within the network is high because multiple operational teams rely on the support that they provide.11 Individual teams or cells, on the other hand, have less connection to the network. This makes finding them a more formidable task. The section has a number of analytical tools, such as the association matrix for mapping the network and finding its key nodes (who may become HVTs).
One of the greatest challenges in COIN is to identify those pockets of the population that indirectly or secretly provide support to the insurgency. Winning over the population denies the insurgents their base of support. To do this, U.S. forces must obtain sufficient cultural intelligence to gain rapport, trust and credibility as an ally of the HN. Cultural missteps impair our relationship with the HN and the people. The people have to believe that the government can fulfill their needs and personal interests. “We never do a good job of cultural intelligence: of understanding what makes people tick, what their structure is, where authority lies, what is different about their values, and their way of doing business.”12
We have to target the people’s support, which is the center of gravity for both the HN government and the insurgents.
Targeting. Owing to the demands of the “three block war,” 13 in which U.S. forces could find themselves providing humanitarian assistance, conducting peace operations and fighting a mid-intensity battle simultaneously, targeting has become more complex. It also demands much more from the intelligence community. With the full-spectrum operations required by COIN, U.S. forces do two types of targeting:
- Lethal—targeting of key leaders and nodes (“kill/capture,” raid)
- Nonlethal—gaining support from the population (“hearts and minds”)
The obvious difference in the two comes in the “deliver” phase. One type of targeting uses combat operations (maneuver and firepower) to destroy, while the other uses nonlethal fires (IO and PSYOP) and CA to persuade. The “detect” phase, however, is also different. The first target is threat-based, but the second considers the neutral population as the target audience. The first type requires the tracking of certain key leaders, while the second type requires an understanding of the environment and the people. The first poses technical challenges; the latter is conceptually difficult.
In order to maintain contact with key leaders or other HVTs, the targeting process in COIN more closely follows “decide, detect, track, deliver, and assess,” instead of the cold war “decide, detect, deliver, and assess.” The change places greater demands on intelligence assets to provide an “unblinking eye” or continuous surveillance of either fixed or moving targets. We know that lethal targeting does not itself provide a solution in COIN.14
We have to target the people’s support, which is the center of gravity for both the HN government and the insurgents. Understanding how factors like culture, religion, and tribal structure cause different behaviors and perceptions is difficult; it requires education and experience. Intelligence sections should seek out a HN military counterpart (English-speaking or not), other government agencies, nongovernmental organizations, immigrants within the ranks, or others who have area expertise.15
Having contributed to the “detect” phase of targeting, the intelligence analyst is still not finished the “assess” phase is critical in COIN. Instead of merely doing a battle-damage assessment, the analyst must anticipate the reaction of key groups and second- and third-order effects. A UAV camera will not pick up the most important effects. Intelligence analysts must be the commander’s experts on culture and be able to predict the consequences of servicing targets.
A critical aspect of targeting the insurgents and the population is that both groups form part of a larger social network. Killing or capturing a key leader could generate ripple effects throughout that network and outside it. Targeting certain groups through nonkinetic means will also affect members of other groups that because of fear, insult, or jealousy, develop a connection to the event.16 Using link analysis, the analyst should try to anticipate these unintended consequences so the commander can more accurately assess his operational risk. With proper intelligence support, targeting allows us to assist the HN government to secure popular support, which, once accomplished, is decisive.
Conclusion
Almost overnight, it seems, MI analysts have gone from templating Soviet motorized rifle divisions to assessing the capabilities of clans, tribes, gangs, and militias. The practice of intelligence has evolved from a military science in conventional operations to a military art in COIN. With that change came the challenge of learning about different peoples and their environments.
In COIN, the environment is as important as the enemy, because the neutral majority, the center of gravity, resides there. COIN requires an appreciation of cultures, religions, tribes, classes, ethnicities, and languages, so that the people will view U.S. forces and their own government positively and work against the insurgents. Knowledge of the population, social networks, and the insurgency helps us to highlight the importance of human factors in fighting an insurgency. Consequently, most intelligence in COIN is collected by HUMINT, including information from Soldier debriefings and reporting. The other intelligence disciplines work in support to confirm or deny HUMINT reporting.
To target the population effectively, intelligence professionals use all-source intelligence gained from HN, joint service, interagency, and multinational partners. Tearing down the walls between these groups and fusing intelligence enables effective targeting. Targeting the enemy and the population through lethal and nonlethal means results in a weakened insurgency that has been denied its base of support. Intelligence and operations, working closely together and with the HN, bring about this end state.
Notes
- David Kilcullen, “Twenty-Eight Articles: Fundamentals of Company-level Counterinsurgency,” Military Review (May-June 2006): 104. Kilcullen notes, “Intelligence will come mostly from your own operations, not as a product prepared and served up by higher headquarters.” A number of active-duty general officers in intelligence and Special Forces concur with that assessment.
- These may range from newly hung posters of a particular leader of coalition concern or population movements into or away from the town.
- E-mail to the authors, 9 April 2006. Cross-cueing refers to tasking more than one collector to confirm or deny information coming from another.
- E-mail to the authors, 20 April 2006.
- E-mail to the authors, 19 April 2006.
- The JIATFs in Afghanistan and Iraq work together through working groups, targeting meetings, and operations and intelligence planning. JIATF responsibilities include collection, targeting, and development of actionable intelligence.
- “Area of interest—The geographical area from which information and intelligence are required to permit planning or successful conduct of the commander’s operation. The AI is usually larger than the command’s AO and battle space; it includes any threat forces or characteristics of the battlefield environment that will significantly influence accomplishment of the mission.” FM 34-130, Intelligence Preparation of the Battlefield (Washington, DC: U.S. Government Printing Office, 1994), G-4.
- Kilcullen, 103.
- For a discussion on this in the context of Operation Iraqi Freedom, see Peter W. Chiarelli and Patrick R. Michaelis, “The Requirement for Full-Spectrum Operations,” Military Review (July-August 2005): 3.
- Intelligence sections use patterns of operation, or tactics, techniques and procedures, in lieu of threat doctrine. Once portrayed graphically, the product becomes a doctrinal template. See FM 34-130, 2-1–2-2.
- In social-network theory, such a node would score a high Eigenvector centrality, a number that measures the node’s importance within the network.
- Retired GEN Anthony Zinni, U.S. Marine Corps (USMC), quoted in Robert F. Baumann and Lawrence A. Yates, My Clan Against the World: US and Coalition Forces in Somalia (Fort Leavenworth, KS: Combat Studies Institute Press, 2004), 49.
- This term was coined by retired GEN Charles Krulak, USMC, to describe a construct of post-cold war conflicts that demanded full-spectrum operations simultaneously. “In one moment in time, our service members will be feeding and clothing displaced refugees—providing humanitarian assistance. In the next moment, they will be holding two warring tribes apart—conducting peacekeeping operations. Finally, they will be fighting a highly lethal mid-intensity battle. All on the same day, all within three city blocks. It will be what we call the three block war.” Charles C. Krulak, “The Three Block War: Fighting In Urban Areas,” presented at the National Press Club, Washington, D.C., 10 October 1997, Vital Speeches of the Day, 15 December 1997, 139.
- As the early 20th-century author and theorist General Sir Charles Gwynn notes, the use of military force must be kept to an absolute minimum because “the military object is to reestablish the control of civil power and secure its acceptance without an aftermath of bitterness.” Sir Charles W. Gwynn, Imperial Policing (London: MacMillan and Company, 1934), 13.
- New York Times columnist Tom Friedman observed the practice and consequence of making lethal targeting the primary focus at the operational level: “Have you noticed how often Israel kills a Hamas activist and the victim is described by Israelis as a ‘senior Hamas official’ or a ‘key operative’?... By now Israel should have killed off the entire Hamas leadership twice … [The result is] something I call Palestinian math: Israel kills one Hamas operative and three others volunteer to take his place, in which case what Israel is doing is actually self-destructive,” New York Times, 15 June 2003.
- If limited area knowledge exists at home station, analysts should make maximum use of written periodicals and products, area-studies departments at universities, immigrant groups and Peace Corps volunteers.
- Examples of this could include a supportive tribe’s anger at numerous government projects and funds for building infrastructure going to a competing tribe that does not support the coalition.
Author’s note: What I have chosen to call “ethnographic intelligence” might be more accurately described as “ethnographic information,” since much of the content involved in analyzing a hostile network will be open-source. I have chosen to retain “intelligence,” however, to indicate the military utility of the content involved.
Major Dan Zeytoonian, U.S. Army, is a Military Intelligence officer who has served in various command and staff positions within the XVIII Airborne Corps and was deployed to Haiti for Operation Uphold Democracy. All the authors have worked for or with conventional military forces, special operations forces, and intelligence agencies at various levels. Their collective operational deployments include Afghanistan, Africa, Bosnia, Georgia, Haiti, Iraq, Korea, and Kosovo. The authors thank Lieutenant General Keith Alexander, retired Major General James Marks, and retired Colonel Rick Allenbaugh for their input to this article.
Back to Top